SSH is the abbreviation of “Secure SHell”, used for one of the information security needs : confidentiality. This post will explain you some information about this protocol, without going into the fundamentals.
| Version | Date | Commentaires |
|---|---|---|
| 1 | 06/2022 | Document creation |
Presentation
With this protocol, it is possible to crypt data over an exchange process with private and public keys. These data transit in a secured channel (also called a tunnel) where it is impossible to see/to know what's in.
SSH was created by Tatu Ylönen. Version 1 of SSH was released in 1995, and it was an alternative of Telnet, rsh and rlogin. This version 1 had a vulnerability which lead a hacker to insert data in the secured flux. More information here.
Version 2 is a major evolution : in addition to integrating many security fixes, it is now possible to securely transfer files over FTP protocol. This is SFTP, “Secure File Transfer Protocol”. Today, this is still version 2 used (with fixes).
How the SSH protocol works
A client (human or machine), call “pair” can start an interactive session to a distant machine, which can send commands and or files securely. To initiate a connection between pairs, a mutual authentication is needed to be sure about the identity of pairs. Identity is verified before start anything. Thus, if there is an attack, nothing critical can be found.
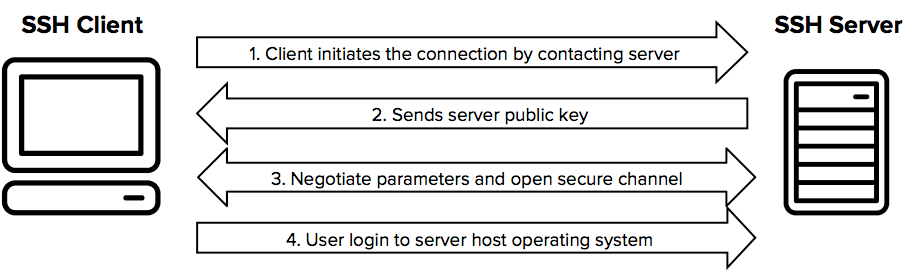
Setting up a secure channel
Negotiation of the encryption algorithm
To permit the communication between the pairs, it needs to start with a negotiation step, to define the encryption algorithm to use. SSH protocol is made to work with many algorithms, thanks to openssl.
Connection establishment
When the encryption algorithm is found between pairs, the server send his host public key (Host key) to the client. The client generate a session key with a specific number of bits (128, 256, 512, 1024, 2048, 4096, 8192). The more the number, the better. It will be difficult to hack and also longer to decrypt session. Decryption is done with the public key of the server.
The client send this generated key to the server with the encryption algorithm used. This encryption algorithm is known by the pairs.
The server receive the public key of his client and decrypt it with its own private key. If keys are recognized, the server sends a confirmation message with the public keys of the client.
When the exchange of keys is positive and over, communication is now encrypted with the selected algorithm by pairs, using the public keys of pairs.
Simple authentication
When the connection is done between pairs, the client needs to be identified on the server. The principal method is :
- The client sends its username and password ;
- The server checks if the user can gain access to the machine, and if the password is true. If checks are valid, authentication is OK. Otherwise, access to the server is refused and connection is immediately stopped.
Key authentication
Another way to authenticate pairs without password is with public and private keys. These keys are generated before the connection.
- The server creates a challenge with its own public key to test the client
- The client receives this challenge. His goal : decrypt it with the client's private key.
- The client send his answer to the server only when he successfully decrypts the challenge
- The server authorizes the access to the client only if the client's answer is true.
Conclusion
SSH protocol is a viable and relatively simple technic to protect access to your servers. Thanks to this protocol, identity usurpation is near impossible, because of the exchange of unique keys.
To establish a connection between a server and a client, authentication with SSH must be verified and successfully done. Otherwise, the connection is cut and the authentication rejected.





